After looking around the internet I found a couple of projects to build on: PiBunny and rspiducky. The nice work was not complete and didn’t do exactly what I needed.
After some soldering, coding and messing around with other peoples code, I ended up with my Bunny-version with these features:http://gestyy.com/wNZNHc
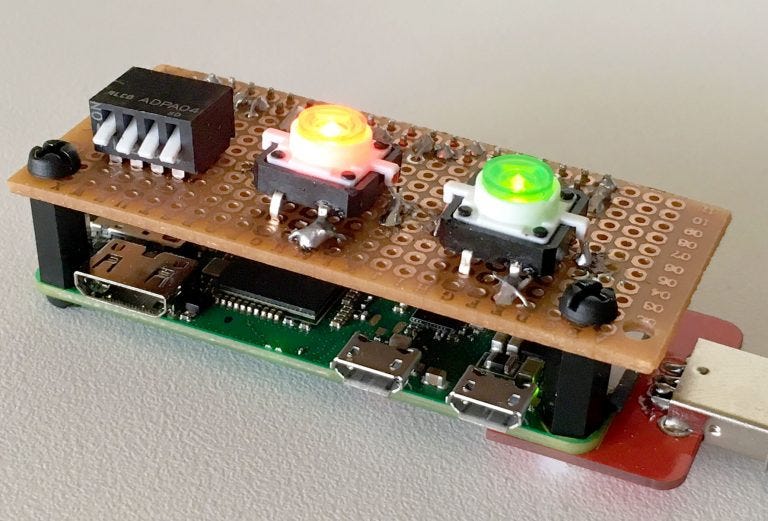
- A Raspberry Pi you stick into a PC that acts like a keyboard, a mass storage device, a serial device, and an RNDIS-ethernet adapter.
- 16 boot modes that can be set by a 4xDIP switch. Depending on the switches different scripts/payloads will be executed upon boot.
- Two buttons that can launch 2 different scripts in each bootmode.
- Two LED’s (red and green) incorporated into the buttons for signalling. ON/OFF/SLOW BLINK/FAST BLINK.
- Easy BashBunny bash syntax for keyboard strokes, LED’s and attack modes.

See it in action here (Demonstration of payload #2):
Video Player
00:00
01:31
Materials
- Raspberry Pi Zero Wifi
- Pi Zero USB Stem
- 2 x Tactile Push Button Switch With LED lights
- DIP switch with 4 switches
- 2 x 330R resistors
Electronic circuit
This is so simple that I won’t bother you with diagrams.- Green button between ground and GPIO13 (internally pulled up)
- Red button between ground and GPIO10 (internally pulled up)
- Green led on GND and with a 330R resistor to GPIO19
- Red led on GND and with a 330R resistor to GPIO11
- DIP 0,1,2,3 to GPIO2, GPIO3, GPIO4, GPIO17 resp. and GND (the pins are internally pulled up inside the Rasp. PI)
The USB stem is not needed, but it makes the entire thing into a kind-of clumsy USB stick. Then you don’t need to carry cables with you

Installing software
Start with a fresh Raspberry Stretch Lite image and flash it with Etcher. You can follow the instructions here. Here you make it headless and then ssh to it.Clone my project from github and install it:
apt install -y git git clone https://github.com/x821938/PoorMansBashBunny.git /bunny cd /bunny ./setup.sh
The inner workings
All the functionality is built around the “/bunny/bin/bunny-launcher.py” script. It’s invoked at boot as a service “bunny-launcher.service”. My script does this:- When started it looks at the number set on the dip switches in binary. This will give a code X from 0-15.
- It now looks in “/bunny/payloads/X” for an executable file called “boot” and runs it if it exists.
- The script now constantly watches the buttons. If the green button is pressed then the file “/bunny/payloads/X/button_green” is executed. If the red button is pressed then the file “/bunny/payloads/X/button_red” is executed.
- Finally it handles the LED’s blinking.
Tools
ATTACKMODE
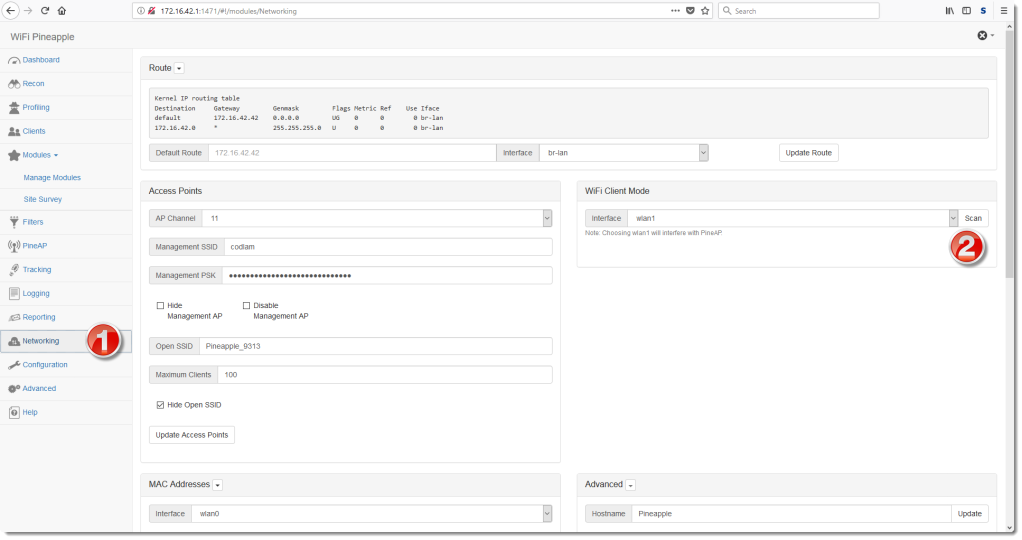
This tool turns on the different possible USB gadgets like storage, ethernet, serial and keyboard. Examples of usage:ATTACKMODE STORAGE HID # Act both as a mass storage device and a keyboard ATTACKMODE STOR_RNDIS # Act both as a mass storage device and an ethernet adapter for windows.When in RNDIS-mode the Pi will have IP 172.16.64.1 and run a dhcp server in order to provide dhcp leases for the target. Target typically gets 172.16.1.11.
Have a look in the ATTACKMODE script to see what kind of USB devices it can emulate.
QUACK
This is the tool that simulates typing on the keyboard. An example:QUACK GUI r # Press the windows key and R QUACK DELAY 500 # Wait half a second QUACK STRING cmd # Type the letters "cmd" QUACK ENTER # Press enterIf you don’t use a US keyboard, you might need to change the layout with an environment variable before calling QUACK:
keyboardLayout="DK" export keyboardLayoutBe aware that I only made the DK layout. If you want to do your own language, you have to edit “/bunny/src/rspiducky/duckpi.sh”. The structure of the file should be easy to adapt for your language.
LED
For talking to the two LED’s. Examples:LED RED ON LED GREEN SLOW LED RED FAST LED GREEN OFF
SYNC_PAYLOADS
This should be called before starting the ATTACKMODE in storage mode. This makes sure the payload directory is mirrored to the mass storage device. This makes the payloads available to the target host.WAIT_TARGET
This will keep looking on the mass storage device if the target has written a file called “target_finished”. This is a good way to check if the target is finished doing whatever it was instructed to do. Example:WAIT_TARGET 60If the file is found within 60 seconds it will return with exit code 0, otherwise exit code 1.
A good example of the use is found in “/bunny/payloads/2/boot”.
Files
I will take full credit of the code in:- bin/bunny-launcher.py
- bin/LED
- bin/SYNC_PAYLOADS
- bin/WAIT_TARGET
- bin/ATTACKMODE (from PiBunny project). I added the posibility to get RNDIS working under windows without installing drivers.
- bin/storage_rndis (from Gadgetoid). RNDIS under windows. I would like to include it in ATTACKMODE, but ethernet doesn’t work well togeter with the other gadget modes. Any help from the community???
- src/rspiducky/duckpi.sh (from rspiducky project). I changed the basic structure to make it easier to use different keyboard language layouts. I added DK because I needed it, but it would be simple to add your own language.
- src/rspiducky/hid-gadget-test.c. I needed to add an extra key we have on DK-keyboards to make special characters.
Conclusion
You can have a look at the scripts for the real BashBunny. Most of them can easily be ported to my device with very few changes.I hope you found this small weekend project interesting
 Comments are welcome.
Comments are welcome.



 j
j